Breach and Attack Simulation
Simulate attacks to measure and optimize the performance of your security controls.

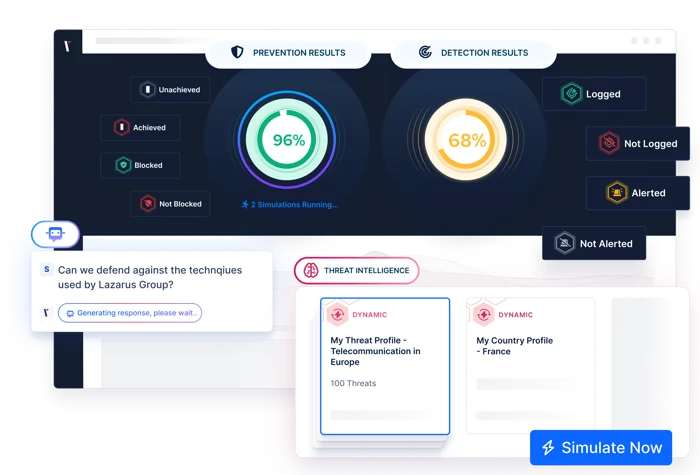
What is Breach and Attack Simulation?
Security controls are fundamental to every organization’s defense against cyber threats. However, security teams often lack assurance that the tools they rely on daily work as they need them to.
Breach and Attack Simulation (BAS) is the automated simulation of cyber attacks to validate that controls such as firewalls, SIEMs, and EDR tools are working and performing optimally.
Reasons to Validate Your Controls:
- Configure settings to your environment
- Improve efficacy over time
- Reduce the risk of IT drift
Benefits of BAS for Security Control Validation
Prove that controls are working as you expect.
Measure readiness to prevent and detect threats.
Quickly respond to changes in the threat landscape.
Get the best ROI from your investments.
Why Security Controls Require Validation
Ever-evolving attacks and daily changes across IT environments mean that the configuration of security controls needs to be constantly reviewed and updated. Firewalls, SIEM, and EDR solutions are not ready to work out of the box and must be tuned regularly to perform effectively.
With security control validation, consistently identify policy gaps that impact the effectiveness of your controls and get action mitigations to reduce the time and effort it takes to optimize them.
Automated Validation Is Essential
While occasional penetration testing and red teaming assessments may provide some insights to help you test the effectiveness of your security controls, the pace of new threats means that a more proactive approach is needed.
Powered by Breach and Attack Simulation, the Picus Security Validation Platform simulates attacks automatically and consistently. Measure security control effectiveness at any moment and benefit from actionable insights to optimize your prevention and detection capabilities.
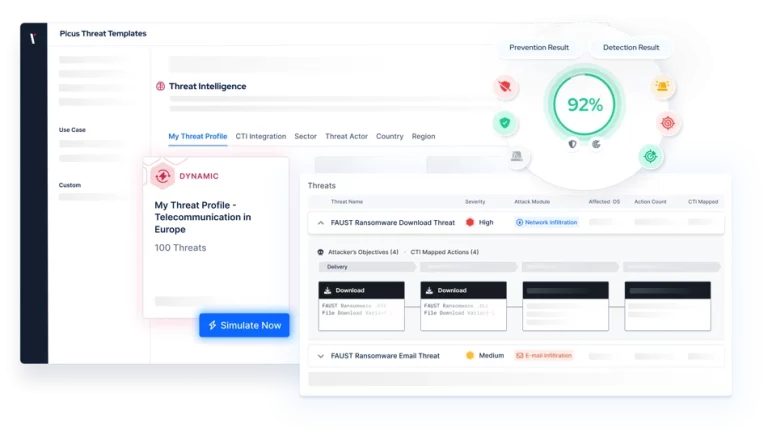
How Picus Helps
Ensure that your controls remain effective with Breach and Attack Simulation.
By simulating thousands of threats and attack techniques, Picus provides assurance that your prevention and detection controls are working as you need them to.
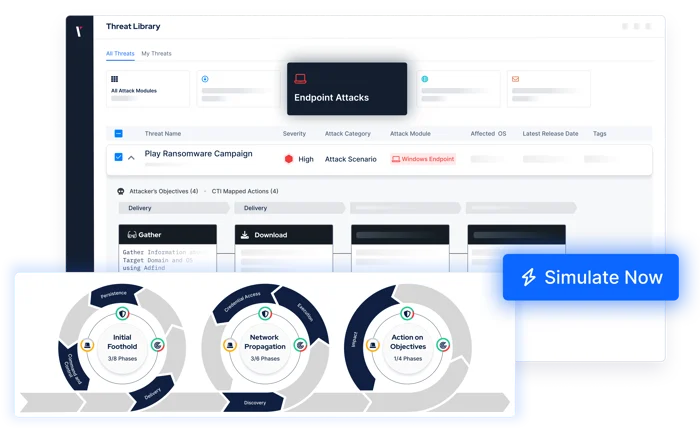
SEE OTHER USES CASES
Address Challenges with Security Validation
See and prioritize exposures across your security operations.