Pen Testing Automation
Scale your manual penetration testing program with automated security validation.

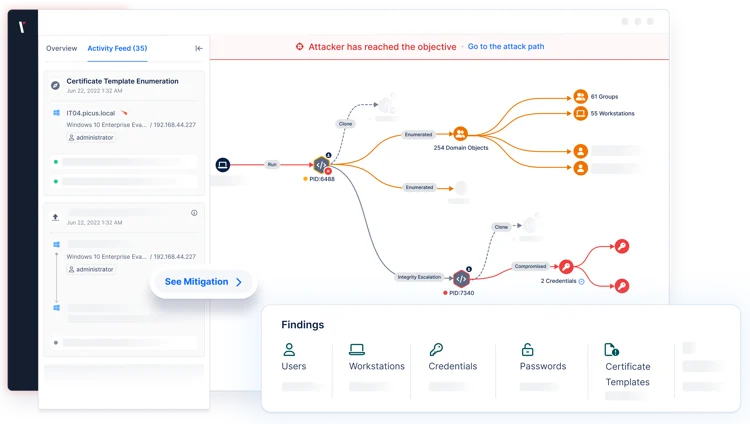
Get More Outcomes From Your Testing
Penetration Testing and other human-led security assessments help organizations identify vulnerabilities and comply with information security regulations. However, the scope and cost of these assessments can prohibit them from being performed regularly.
Attack simulation broadens the scope and frequency of testing programs, enabling security teams without offensive security skills to obtain consistent validation insights.
Automate Pen Testing to:
- dentify and address risks sooner
- Alleviate manual testing requirements
- Broaden attack surface visibility
Benefits of Pen Test Automation
Expand the scale and scope of testing.
Quantify and measure risks.
Insights when you need them.
No ethical hacking expertise required.
Why Manual Pen Testing is Not Enough
While manual penetration testing remains a key way to assess your cyber security through the eyes of a human attacker, the time it takes to conduct tests manually means that assessments are performed at a single point in time and have a narrow scope.
With pen testing automation, scale the breadth and depth of your testing program and benefit from consistent insights that enable you to identify and address risks sooner.
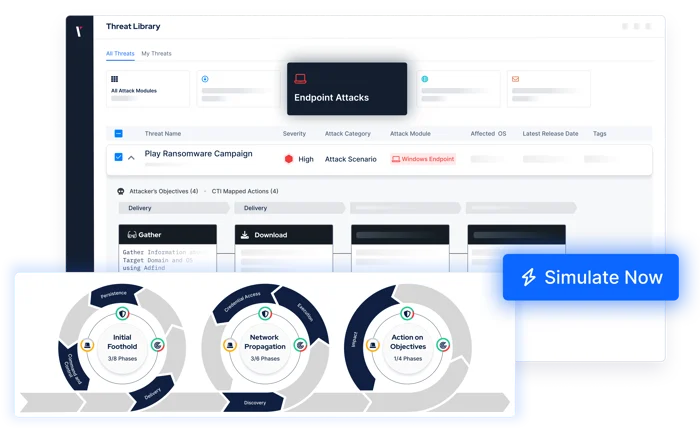
How Picus Helps
By automating penetration testing, Picus supplies the insights you need to measure and optimize your security posture on a consistent basis.
At the click of a button, simulate thousands of real-world threats and attack techniques across the cyber kill chain.
For a holistic view, validate your security outside>in and inside>out. Also benefit from actionable insights to prioritize vulnerabilities, optimize security controls, and more.
Security Validation Across Your Internal and External Attack Surfaces
Uncover exposures across your IT environment.
Security Controls
Validate the effectiveness of your controls to prevent and detect network infiltration, web application attacks, data exfiltration, and more.
Internal Network
Validate your security through the eyes of an evasive attacker with initial access to your organization's network.
Cloud Environments
Validate IAM policies and configurations with attack simulation for AWS, Azure and GCP.
Assets
Broaden visibility of the assets attackers could target to compromise your environment.

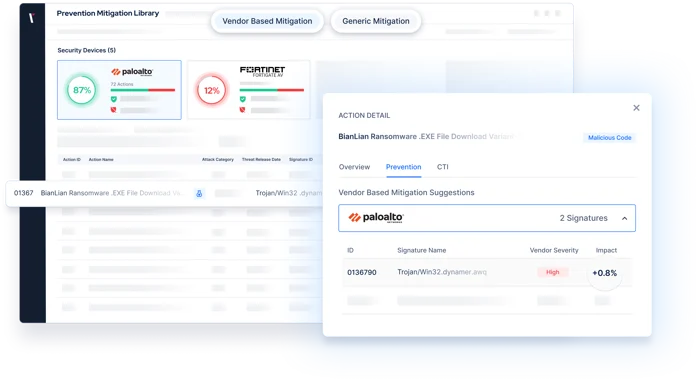
Actionable Insights. Not Generic Guidance.
Manual penetration testing engagements can fail to provide the metrics you need to quantify your threat readiness.
By choosing to automate your penetration testing program with Picus, measure your cyber risk in key areas, easily track improvements, and evidence your security posture.
Actionable remediation and mitigation insights provide the support you need to address risks quickly and effectively.
"Companies should embrace automated continuous testing to protect against longstanding online threats."
Cybersecurity and Infrastructure Security Agency (CISA)

SEE OTHER USES CASES
Address Challenges with Security Validation
See and prioritize exposures across your security operations.