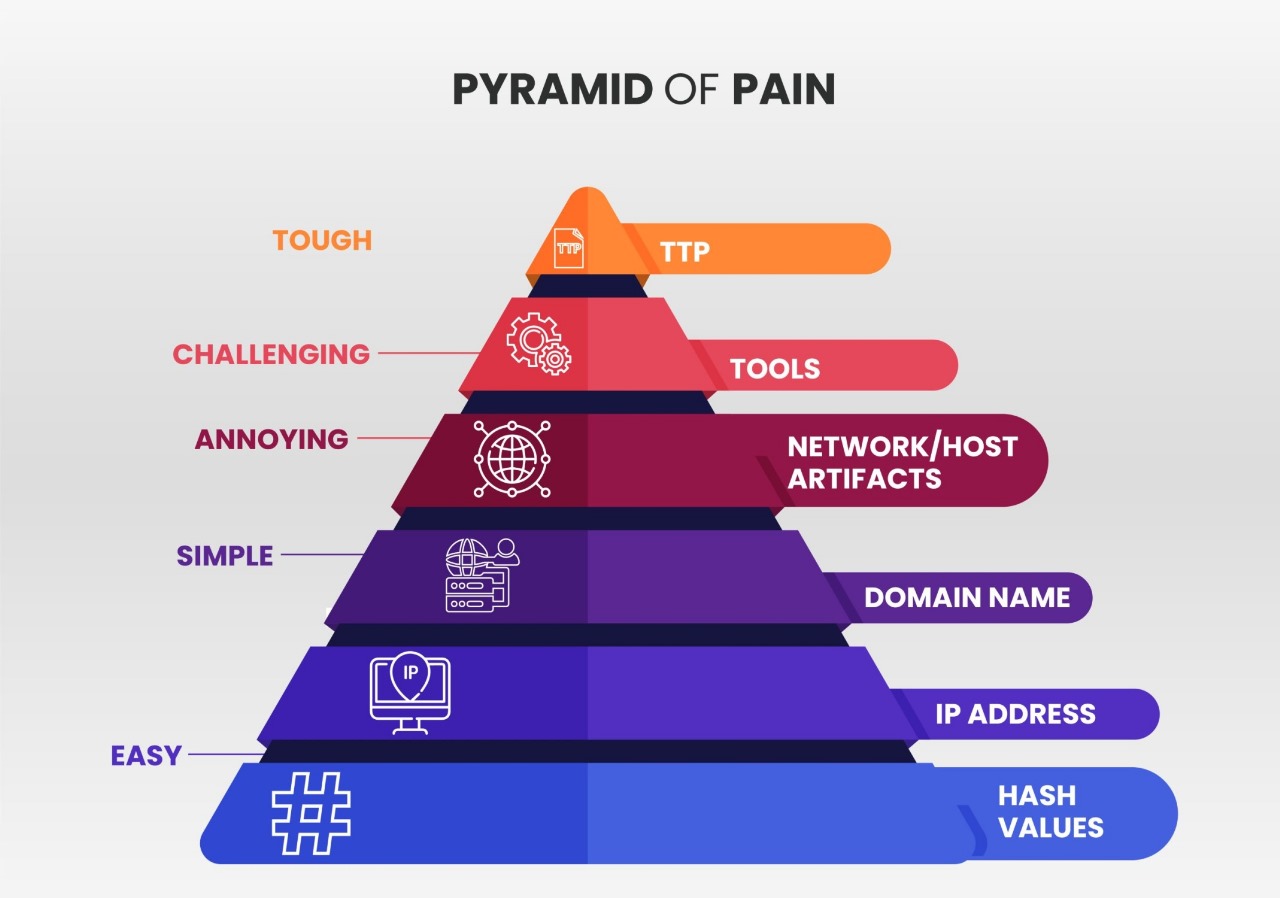
In the ever-evolving landscape of cybersecurity, the Pyramid of Pain is a crucial framework for understanding and mitigating threats. Developed by David J. Bianco, this model categorizes indicators of compromise (IOCs) into six levels, each representing different types of data that can be used to detect and respond to cyber threats. The higher up the pyramid an IOC is, the more pain it causes adversaries when disrupted, hence the name. By focusing on these upper layers, organizations can inflict significant difficulties on attackers, making it harder for them to achieve their objectives.
How Does the Pyramid of Pain Work?
The Pyramid of Pain operates on the principle that not all IOCs are created equal. At the base of the pyramid, we have simple IOCs like hash values and IP addresses, which are relatively easy for attackers to change and evade detection. As we move up, the pyramid includes domain names, network/host artifacts, and tools, culminating in tactics, techniques, and procedures (TTPs) at the apex. Each level represents increasing difficulty for adversaries to alter their methods and remain undetected. Disrupting higher-level IOCs, such as TTPs, forces attackers to fundamentally change their approach, significantly hindering their operations and increasing their operational costs. By focusing on these higher levels, organizations can deliver more impactful blows to cyber adversaries.
TTPs are at the apex, representing the highest level of sophistication in an adversary’s operations. Disrupting TTPs forces attackers to fundamentally alter their methods, which is not only difficult but also time-consuming and resource-intensive. Therefore, focusing on TTPs is the most effective strategy in threat hunting and mitigation.
However, the challenge lies in identifying and responding to these high-level IOCs. This is where advanced cybersecurity solutions and threat intelligence platforms come into play. By leveraging machine learning, behavioral analysis, and automated response systems, organizations can enhance their ability to detect and neutralize threats at the higher levels of the pyramid. Continuous monitoring and proactive threat hunting are essential in staying ahead of sophisticated adversaries who constantly evolve their tactics to bypass traditional security measures.
At Terrabyte Group, we understand the complexities of modern cybersecurity challenges. That’s why we have partnered with Picus Security to offer cutting-edge solutions designed to tackle threats at every level of the Pyramid of Pain. Together, we provide comprehensive threat intelligence and advanced defensive measures that ensure your organization stays protected against even the most sophisticated cyber-attacks. Contact us today to learn more about how our collaborative efforts can fortify your cybersecurity posture and keep your digital assets safe.